Assessing Cyber Risk in Your Suppliers: Why & How to Transform Your Practices

The growing dependence of companies on vast, interconnected digital ecosystems is radically reshaping how cyber risk must be approached. The 2025 edition of the TPRM Observatory, conducted by Board of Cyber and CESIN, confirms a now-central trend: cyber risk from suppliers is no longer peripheral — it has become strategic, and is now recognized as a systemic risk by most organizations. Yet despite this awareness, current assessment methods remain largely suboptimal and insufficiently industrialized.
Context: Cybersecurity & TPRM as Structural Challenges
The generalization of digital services, outsourcing of processes, and technological standardization have significantly widened the attack surface of organizations. According to the Observatory, 81.8% of companies consider third-party risk to be important or very important TPRM Observatory 2025 _ CESIN …
At the same time, regulatory pressure is intensifying: NIS2, DORA, the AI Act… These frameworks demand stronger security and control standards.
This growing maturity is reflected in more structured governance: 60% of companies now centralize third-party risk management, and 54% elevate the topic to the executive committee level TPRM Observatory 2025 _ CESIN …
As a result, supplier cybersecurity is no longer just a technical topic — it’s a governance and resilience issue that involves the entire organization.
New Personas, But Still Limited Methods
The study highlights the emergence of new personas involved in TPRM: beyond CISOs, legal departments, procurement, compliance, and business functions are increasingly engaged. This diversity reflects a desire to address supplier cyber risk in a cross-functional way.
However, despite this mobilization, assessment methods remain overly focused on self-declared questionnaires — tools that are seen as time-consuming, unreliable, and hard to scale.
According to the Observatory:
- 60% of companies still use security questionnaires (declining, but still the majority)
- 75% use a Security Assurance Plan (PAS)
- More objective approaches — SOC 2 certification, audits, external ratings — are on the rise but still a minority TPRM Observatory 2025 _ CESIN …
This paradox illustrates a growing maturity that is still held back by its tools.
The Four Key Challenges of Supplier Cyber Risk Assessment
Surveyed companies consistently point to recurring roadblocks. The 2025 Observatory identifies four major obstacles:
1. Lack of Human & Financial Resources
68% of organizations report lacking the resources to conduct necessary assessments. This structural limitation prevents large-scale supplier risk management.
2. Difficulty Engaging Suppliers
64% struggle to get complete, reliable, or timely responses. Some partners — particularly major cloud providers — even refuse audits or questionnaires altogether.
3. Uneven Maturity Among Third Parties
52% of companies find that their suppliers fail to meet expected security levels. The supply chain remains highly vulnerable.
4. Scaling Issues & Lack of Mutualization
41% cite the inability to industrialize their processes.
And 31% lament the absence of shared platforms to avoid redundant audits TPRM Observatory 2025 _ CESIN …
These insights confirm the urgent need for a new model: supplier assessments can no longer rely on manual campaigns or the goodwill of third parties.
When & How to Identify Your Suppliers’ Cyber Risks
The Observatory reveals that 63% of companies assess fewer than 50 suppliers per year, even though they may have hundreds or thousands. This lack of scrutiny often stems from the limitations of their methodology, which can’t effectively process questionnaire responses — assuming they even get responses.
Yet cyber risk should be assessed at three critical moments:
1. During Supplier Onboarding
Evaluate service criticality, data access, and system integration level.
68% of companies now classify suppliers by risk — a sharp increase TPRM Observatory 2025 _ CESIN
2. Before Contract Signing
Include security clauses, certification requirements, and audit rights.
For 9 out of 10 companies, the contract remains the main governance tool.
3. Continuously Throughout the Relationship
Risks evolve over time: vulnerabilities, incidents, data breaches, infrastructure changes.
Yet today, only a minority of organizations monitor third-party exposure continuously.
The challenge: moving from one-time evaluations to dynamic, ongoing monitoring.
Solution: Automation & Mutualization — The Future of Supplier Cyber Assessment
The Observatory’s conclusion is clear: 80% of companies are open to mutualizing supplier assessments, and 77% want to rely more on recognized certifications (ISO, SOC 2, etc.) to reduce questionnaire use.
Two key trends are emerging:
1. Automating Controls
CISOs express strong demand for tools that can:
- Automatically collect evidence
- Continuously assess security posture
- Generate alerts in case of drift
- Reduce operational workload from questionnaires
- Automate evaluations
This automation is becoming essential to scale up operations.
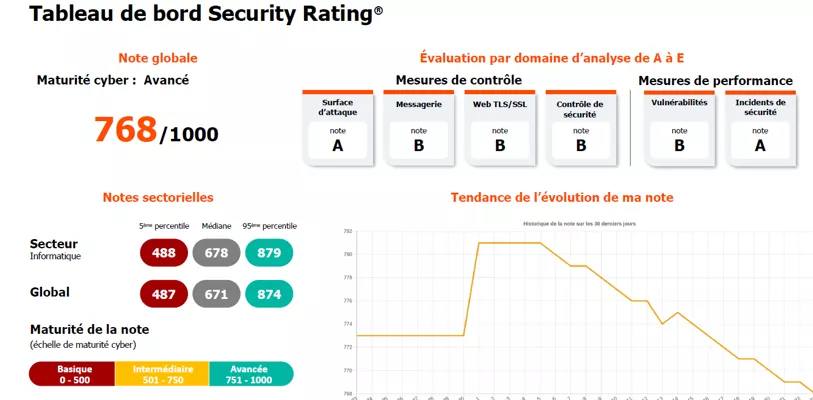
2. Mutualizing Assessments: A Future-Proof Model
The study shows strong support for a shared model based on:
- Common risk frameworks
- Reusable third-party evaluations
- Mutual recognition of certifications
- A trusted institutional environment
As one CISO put it:
“Mutualization is the only viable alternative to an inefficient, time-consuming system that relies too heavily on self-filled questionnaires that serve as little more than a formality.” TPRM Observatory 2025 _ CESIN …
Move to proactive risk management today!
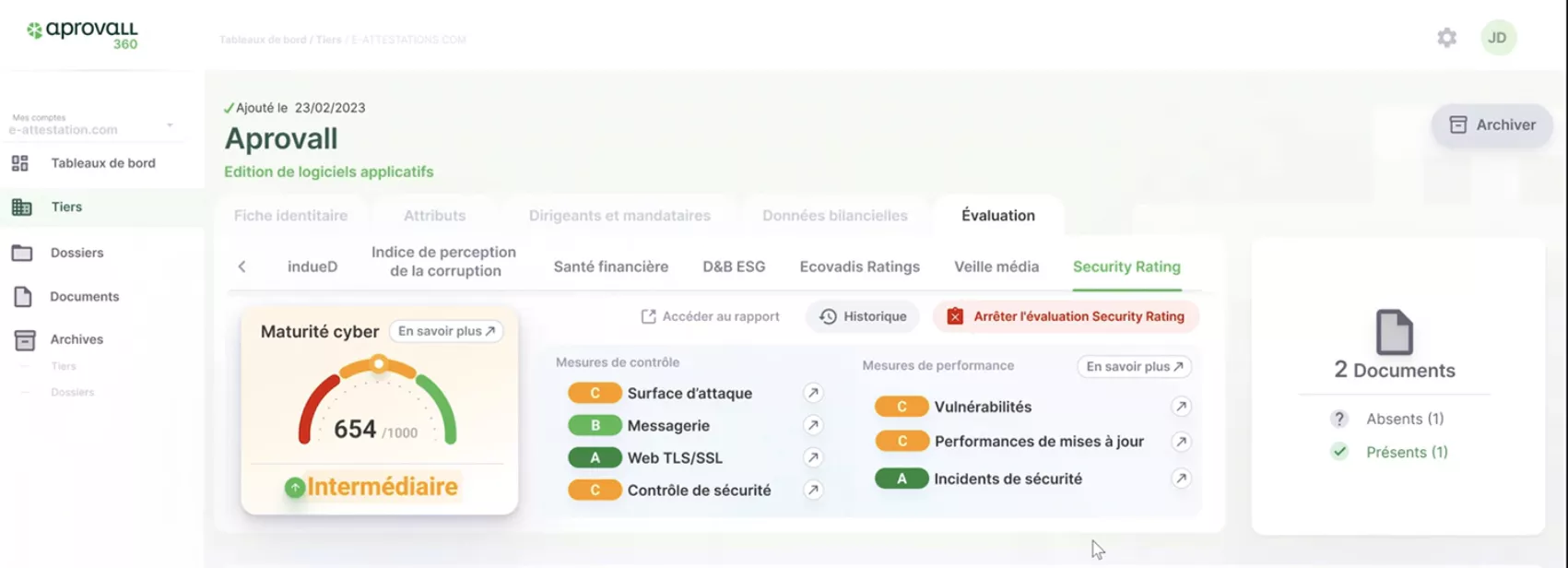
With Aprovall360, benefit from an intuitive and powerful solution designed to meet the requirements of the most highly regulated industries. Don’t just react to risks — anticipate them, measure them, and manage them with confidence.
These articles might interest you
-
 14 September 2024Aprovall supports you in your new due diligence obligations arising from the European CS3D Directive.SolutionsThe Corporate Sustainability Due Diligence Directive, known as “CS3D”, was definitively adopted on Wednesday, April 24, 2024, by the European Parliament. The directive now needs to be officially approved by the Council and signed before being published in the EU Official Journal. It will enter into force 20 days later. Member States will then have […]
14 September 2024Aprovall supports you in your new due diligence obligations arising from the European CS3D Directive.SolutionsThe Corporate Sustainability Due Diligence Directive, known as “CS3D”, was definitively adopted on Wednesday, April 24, 2024, by the European Parliament. The directive now needs to be officially approved by the Council and signed before being published in the EU Official Journal. It will enter into force 20 days later. Member States will then have […]Read more
-
 18 April 2025ESG Strategy for the Supply Chain: Assessment and Management MethodsSolutionsThe ESG strategy (Environment, Social, Governance) has become a fundamental pillar of corporate operational resilience. According to the 2025 Supply Chain ESG Risk Outlook by LRQA, over half of sourcing countries are now classified as high or extreme ESG risk, challenging the common perception that Western markets are inherently safer. This new reality demands a […]
18 April 2025ESG Strategy for the Supply Chain: Assessment and Management MethodsSolutionsThe ESG strategy (Environment, Social, Governance) has become a fundamental pillar of corporate operational resilience. According to the 2025 Supply Chain ESG Risk Outlook by LRQA, over half of sourcing countries are now classified as high or extreme ESG risk, challenging the common perception that Western markets are inherently safer. This new reality demands a […]Read more
-
 06 February 2025Effective Third-Party Governance: A Holistic Approach to Optimized Risk ManagementSolutionsIn a context where 38% of companies have experienced major disruptions due to third-party partners over the past three years, third-party governance is becoming a strategic imperative. This reality is even more critical as 90% of organizations now consider third-party risk management a growing priority. Effective third-party management relies on a holistic approach integrating six key areas of expertise: Legal […]
06 February 2025Effective Third-Party Governance: A Holistic Approach to Optimized Risk ManagementSolutionsIn a context where 38% of companies have experienced major disruptions due to third-party partners over the past three years, third-party governance is becoming a strategic imperative. This reality is even more critical as 90% of organizations now consider third-party risk management a growing priority. Effective third-party management relies on a holistic approach integrating six key areas of expertise: Legal […]Read more
-
 17 March 2025Understanding Third-Party Cybersecurity Maturity: Keys to Effective AssessmentSolutionsThird-party governance has become a major strategic issue in an economic context marked by the growing interdependence between companies and their external partners. According to Gartner, 45% of cyberattacks in 2025 will originate from third parties, highlighting the urgency of a structured evaluation approach. Operational resilience against these threats now requires a shift from simple […]
17 March 2025Understanding Third-Party Cybersecurity Maturity: Keys to Effective AssessmentSolutionsThird-party governance has become a major strategic issue in an economic context marked by the growing interdependence between companies and their external partners. According to Gartner, 45% of cyberattacks in 2025 will originate from third parties, highlighting the urgency of a structured evaluation approach. Operational resilience against these threats now requires a shift from simple […]Read more



